How To Safeguard Your Network from DoS and DDoS Attacks
Introduction to Network Security Threats
The digital age has brought unparalleled convenience and connectivity but has also exposed us to many cybersecurity threats. Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks are among the most disruptive. Understanding these threats and how to protect your network is crucial for maintaining the integrity of your digital assets. These attacks can halt your online presence, resulting in significant financial and reputational damage if not addressed promptly.
Key Takeaways:
- Understanding the fundamental differences between DoS and DDoS attacks.
- Recognizing the signs of an ongoing attack.
- Implementing preventive measures to protect your network.
- Responding effectively to mitigate the impact of attacks.
- Regularly updating your security protocols to tackle new threats.
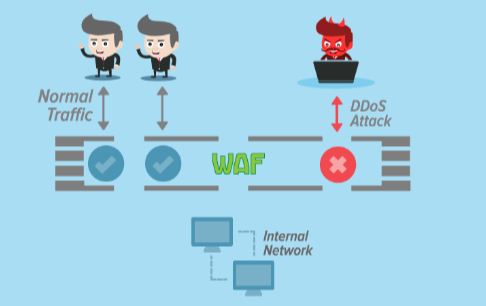
What Are DoS and DDoS Attacks?
DoS attacks aim to overwhelm a network or server with excessive traffic, rendering it unable to respond to legitimate requests. For a comprehensive overview of the differences, see DDS compared with DDOS. A hacker sends more traffic to the intended target than it can handle, causing a service outage. On the other hand, DDoS attacks involve multiple systems, often compromised by malware, working together to flood the target with traffic. The distributed nature of DDoS attacks makes them harder to fend off, as the traffic comes from various sources. These methods can disrupt services for hours or days if not appropriately managed.
Recognizing the Signs of an Attack
Early detection is critical to mitigating the damage caused by DoS or DDoS attacks. Common indicators include:
- Prolonged network performance.
- Unavailability of a particular website.
- A sudden surge in spam emails.
These disruptions can result in significant downtime and revenue loss. Recognizing these signs can save your business considerable time and resources. Anomalies in traffic patterns, mainly originating from multiple geographic locations, can signal a potential DDoS attack. Awareness of these symptoms can help you promptly activate your emergency response plan.
Common Symptoms
- Delayed or failed transactions that frustrate customers and delay business operations.
- Interrupted or dropped connections that can halt communications and critical processes.
- Significant increase in traffic from a single IP range, often a telltale sign of an ongoing attack.
Preventive Measures
Prevention is always better than cure. Implementing robust firewall protections and intrusion detection systems can reduce the likelihood of successful DoS and DDoS attacks. These tools act as the first line of defense, filtering malicious traffic before it reaches critical systems. Regularly updating your software and protocols is also crucial, as hackers constantly evolve their tactics. Outdated systems are more vulnerable to attacks, so staying current with security patches and updates is essential. Using devices like an gsm data reciever can further enhance security by monitoring network traffic and detecting anomalies in real-time.
Read more Healthy Buildings: Creating Sustainable and Comfortable Environments
Implementing Robust Firewalls
- Use hardware and software-based firewalls to add multiple layers of protection.
- Enable automatic updates for firewalls to ensure they can address the latest threats.
Intrusion Detection Systems
- Monitor traffic patterns regularly to identify unusual activities promptly.
- Deploy heuristic detection models that can learn and adapt to new attack patterns.
Effective Response Tactics
If your network is under attack, quick action is vital. Isolate the affected systems and notify your internet service provider immediately. A predefined response plan can dramatically reduce downtime and mitigate the attack’s impact. This plan should include detailed steps for identifying the attack source, isolating affected systems, and rerouting traffic if necessary. A detailed guide on responding to such threats can be found here. Many businesses fail to act swiftly during an attack, exacerbating the damage and extending recovery time.
The Importance of Regular Security Audits
Regularly scheduled security audits help identify vulnerabilities before they are exploited. These audits review your network’s defenses, identifying weak points that attackers could target. Ensuring that your network’s defenses are robust and up-to-date can make the difference between a minor hiccup and a major disaster. Audits should also review incident response plans, ensuring they are comprehensive and current. Regular audits are proactive, preventing security gaps that could lead to significant breaches.
Schedule Regular Audits
- Quarterly network security reviews to stay ahead of emerging threats.
- Automated vulnerability assessments that provide real-time feedback on potential risks.
Staying Informed
The landscape of cybersecurity is ever-changing. Keeping abreast of the latest threats and security trends is crucial for protecting your network. Subscribing to cybersecurity newsletters and attending relevant webinars can provide valuable insights. These resources offer updates on the latest attack vectors and defense mechanisms, helping you stay ahead of cybercriminals. For example, a detailed analysis of contemporary cyber threats can be found here. Industry conferences and workshops are also excellent venues for learning from experts and networking with peers facing similar challenges.
Educational Resources
- Webinars and online courses providing detailed instruction on particular security subjects.
- Industry newsletters that provide regular updates and expert opinions on emerging threats.
Conclusion
In an era where digital threats are ever-present, understanding how to protect your network from DoS and DDoS attacks is essential. By recognizing the signs of an attack and implementing preventive and responsive measures, you can safeguard your digital assets effectively. Stay informed and proactive to ensure your network remains resilient against these and other cybersecurity threats. Regular training for your IT team and ongoing updates to your security strategies are crucial for maintaining solid defenses. Your strategy for network security must evolve along with the ever-changing digital landscape.




